Any university owned facility e g building equipment designated space within a building infrastructure that is not open to the public and has restricted access procedures established for purposes of maintaining the security or confidentiality of the information or other resources contained within it.
Facility access control procedure.
Authentication authentication is the process of identifying an information user by the user presenting credentials.
Access control procedures are the methods and mechanisms used by information owners to approve permission for users to access data information and systems.
These procedures will be contained in the ce s facility security plan.
A standard operating procedure sop for access control.
Information security access control procedure pa classification no.
Additional controls are as follows.
Departments that have special access or key control requirements may need to establish internal procedures to meet those requirements e g.
Purpose and definition of any access control sop.
In a computer system this is most often accomplished by using the unique.
Ces must also implement procedures for control of access to software programs for testing and revision.
09 21 2018 ii identify access requirements with required access levels for each system or application for authorized users to include newly assigned personnel or transfers.
Cio 2150 p 01 2 cio approval date.
This alleviates confusion and facilitates access by ensuring that employees and visitors have appropriate id prior to accessing the facility.
2 1 1 terms overview access control vs.
Sop s were designed to create uniformity of effort and cohesion thus resulting in the continuity of standards these standards would also refer to unit standards tactics.
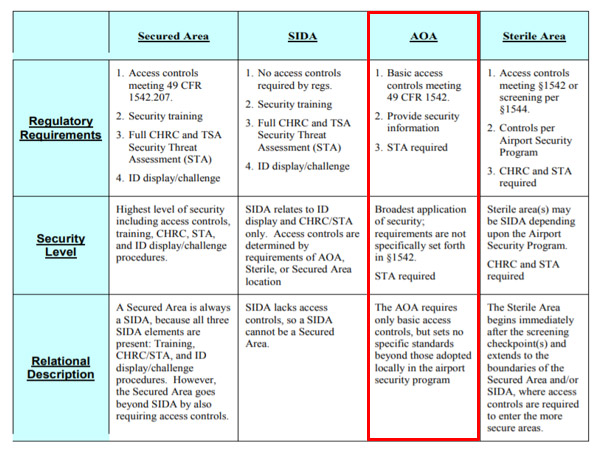
Access control defines a system that restricts access to a facility based on a set of parameters.
Person s access to facilities based on their role or function including visitor access control.
Access control systems include card reading devices of varying.
09 21 2015 cio transmittal no.
Best practices immediate action drills intelligence gathering surveillance and counter.